Fri Jan 19 2018 · 6 min read
Armenia at the Center of State-Sponsored Cyber Attacks

By Samvel Martirosyan
If you follow the media in Armenia, you will get a clear sense that Armenian citizens and organizations come under attack primarily from Azerbaijani and Turkish hackers. From a quantitative perspective, this certainly seems to be true. In the last year alone, hackers from Azerbaijan and Turkey were able to hack several thousand Armenian profiles on Facebook and Instagram. And if we look back over the last 10-15 years, the overriding number of cyber attacks were indeed the work of Azerbaijani and Turkish cyber groups. Until October 2009, when Armenia’s National Security Service (NSS) took over the supervision of Armenia's state cyber space, Azerbaijani hacking groups would collectively attack and breach security networks of official Republic of Armenia and Artsakh state sites. Since the NSS took over, the number of successful attacks decreased drastically.
However, if we look beyond large-scale attacks to the more targeted ones - cyber operations against important state and non-state institutions, as well as individuals - it is possible to highlight a number of well known cases. And behind each of these are state-sponsored hacker groups or even state structures themselves.
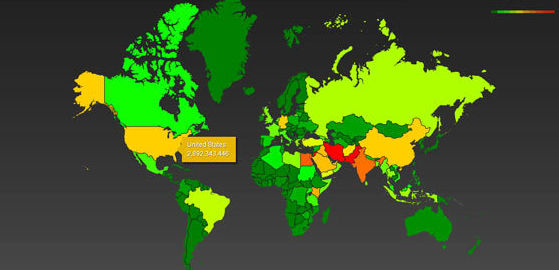
If we examine Edward Snowden’s leaks, we can see that the interest of American security services towards Armenia is above average. Boundless Informant, the National Security Agency’s (NSA) data mining tool, monitors, details and maps by country information it collects from different sources - computer and telephone networks. An image made available by Snowden, shows that in March of 2013, there was an inflow of about 3 billion different kinds of information (intel) from the U.S. alone.
Countries are color coded according to NSA activity in any given month; green for low activity, red for high activity - in the leaked document, Armenia is yellow, like China yet more active than Russia, which is evidence of significant NSA activity regarding Armenia.
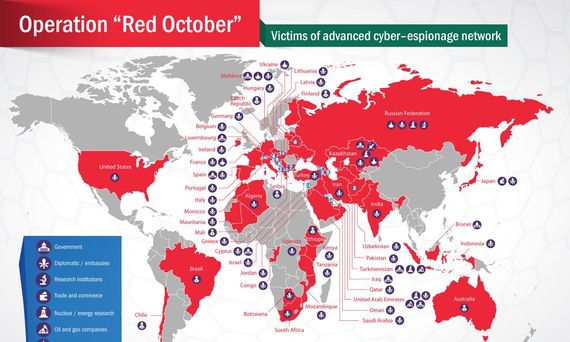
In 2013, Kaspersky Lab’s Global Research & Analysis Team discovered a large scale cyber-espionage network which they called “Red October.” It was able to infiltrate important state and non-state substructures (including diplomatic, governmental and scientific research organizations in different countries, mainly of Eastern Europe and the former USSR) and initiate an elaborate cyber espionage even retrieving deleted files, in case they were of any interest to the creators of the virus.
According to Kaspersky, evidence indicated that the cyber-espionage campaign was active starting from 2007 before being detected in 2013. Armenia made the top ten most infected list with ten cases of infection with the virus. Russia was the most attacked country with 37 cases of Red October infections.
It has never been revealed who launched Red October. Security experts were able to detect traces of Russian in the coding but those could have been intentionally planted in an attempt to divert attention. Moreover, Russia was the main target of this attack. There are plausible traces indicating China’s involvement. Parts of the used technology could be linked to programs used against Tibetan activists and are assumed to be used by China's special services.
In its 2014 report titled, “APT28: A Window Into Russia’s Cyber Espionage Operations?” FireEye, an organization that is specialized in information security, exposed the large-scale international activity of a hacker group, with members of the Armenian military among their targets. The report dealt with APT28 or Fancy Bear, the hacker group now famous for its alleged activity during the U.S. presidential elections. This group is considered by many specialists as a Russian state cyber-group, operating in the interest of the Kremlin: “They compile malware samples with Russian language settings during working hours consistent with the time zone of Russia’s major cities, including Moscow and St. Petersburg.” According to the FireEye study, Fancy Bear hackers had created the fake mail.rnil.am phishing site, imitating the Armenian Ministry of Defense mil.am domain and made it possible to “target members of the Armenian military by hosting a fake login page.” It is not clear what damage the hackers have caused Armenia.
The rnil.am domain is periodically mentioned in different reports, in numerous phishing attacks. For example, it has been used against the Bellingcat organization investigating the downing of the Malaysian Airlines (MH17) aircraft that came down in eastern Ukraine in 2014 in an area controlled by pro-Russian separatists, something Russian authorities were keenly interested in.
In May 2017, the Citizen Lab organization made new discoveries regarding the latest activities of Fancy Bear. This time too, Armenia was on the list of victims. According to the TAINTED LEAKS․ Disinformation and Phishing With a Russian Nexus report, this time the targets were members of the Armenian government and the military. The report states that Armenia was one of the main targets of the phishing attack, with three percent of the attacks being addressed to the Republic (of Armenia). According to available data, high ranking military officials and diplomats are on the list of Armenian victims.
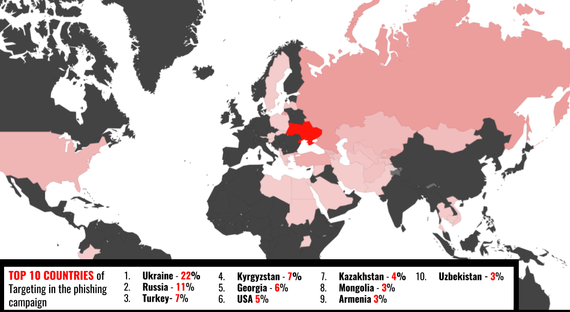
In May 2017, the Citizen Lab organization made new discoveries regarding the latest activities of Fancy Bear. This time too, Armenia was on the list of victims. According to the TAINTED LEAKS․ Disinformation and Phishing With a Russian Nexus report, this time the targets were members of the Armenian government and the military. The report states that Armenia was one of the main targets of the phishing attack, with three percent of the attacks being addressed to the Republic (of Armenia). According to available data, high ranking military officials and diplomats are on the list of Armenian victims.
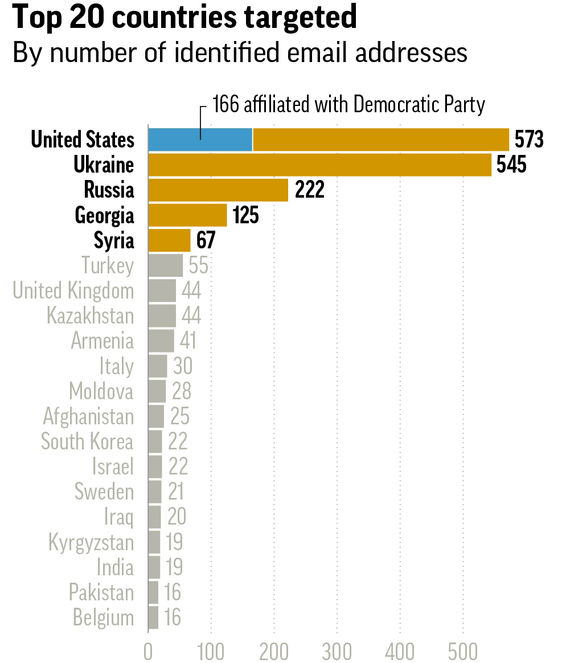
At the end of last year, an article titled “Russia hackers pursued Putin foes, not just US Democrats,” was published by the Associated Press about the Fancy Bear group. Once again, on the list of large scale cyber attacks carried out simultaneously against a large number of countries, there are 41 citizens of Armenia.
The names of the Armenian targets of the attack have not been published but it is known that since 2015, starting with the Electric Yerevan protests, EVN Report Editor-in-Chief, Maria Titizian was one of the targets. According to the information available to us, other than journalists, there are also political scientists and analysts on the list of the 41 individuals, all of whom can be described as Western leaning.
These are the instances of state cyber espionage that we are aware of. Considering how advanced state hacking has become in recent years, it is possible that some of the cyber attacks on Armenia, possibly a considerable amount, have not yet been discovered. It is also evident that Armenia is a subject of interest in almost all major cyber investigations.


